A new cyber threat group called NightEagle APT has been discovered exploiting a Microsoft Exchange flaw to target Chinese sectors.
Security researchers at QiAnXin’s RedDrip Team revealed the attacks at the CYDES 2025 cyber defense conference in Malaysia.
The group, also known as APT-Q-95, has been active since 2023 and moves its infrastructure at a fast pace.
QiAnXin said NightEagle earned its name from its stealthy night-time attacks and speed, like that of an eagle. These attacks have focused on Chinese government, defense, artificial intelligence, and semiconductor sectors.
The primary goal of NightEagle APT Microsoft Exchange attacks is to steal sensitive information from high-value targets.
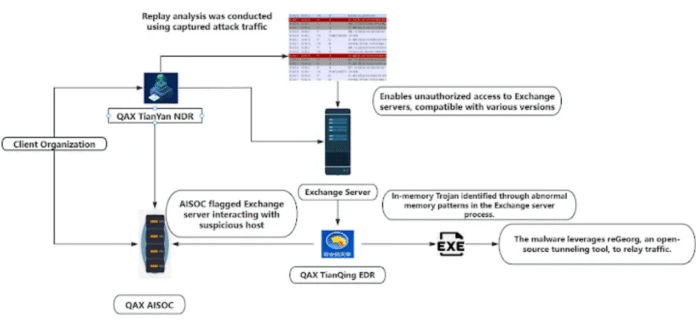
QiAnXin began its investigation after spotting a modified Chisel utility running on a client system. The Go-based tool made to run every four hours, enabling hidden access to internal networks.
Attackers had altered the tool’s source code, hardcoded login details, and linked it to a specific command-and-control (C&C) server. By doing this, they created a direct tunnel to internal systems via port mapping on the infected device. The malware deploy using a .NET loader embedded in Microsoft Exchange’s Internet Information Services (IIS).
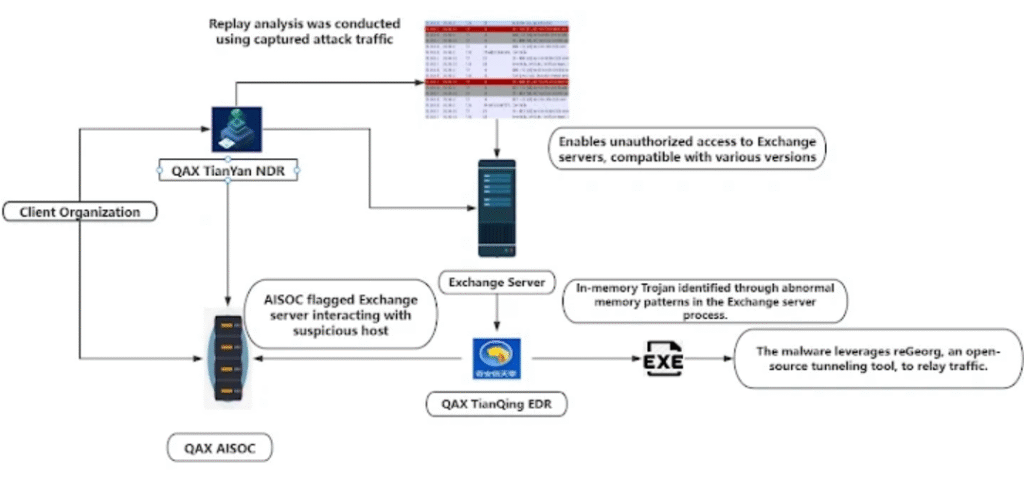
Researchers uncovered a zero-day vulnerability used to gain access to the Exchange Server’s machineKey. This allowed NightEagle to deserialize the server and install backdoors across compatible Exchange versions. The attacker could then access and read emails from any user on the compromised server.
QiAnXin believes the operation is based in North America, citing activity between 9 p.m. and 6 a.m. Beijing time.
So far, Microsoft has not released a statement on the exploit or confirmed any patch details. The discovery of NightEagle APT Microsoft Exchange operations highlights the growing threat of targeted attacks using zero-day flaws. Experts urge organizations using Microsoft Exchange to monitor traffic, update systems, and audit suspicious IIS activity.